-
Business Risk Services
Our Business Risk Services team deliver practical and pragmatic solutions that support clients in growing and protecting the inherent value of their businesses.
-
Consulting
Tailored consulting solutions that deliver measurable results through digital, regulatory and strategic transformation.
-
Corporate Finance and Deal Advisory
We offer a dedicated team of experienced individuals with a focus on successfully executing transactions for corporates and financial institutions. We offer an integrated approach, with our corporate finance specialists working seamlessly with tax and other specialists to ensure that every angle is covered.
-
Forensic Accounting
We have a different way of doing business by delivering real insight through a combination of technical rigour, commercial experience and intuitive judgment. We take pride in delivering responsive and tailored solutions to all our clients, capitalising on the wealth of experience housed within our Belfast and wider Forensics team
-
Restructuring
We work with a wide variety of clients and stakeholders such as high street banks, private equity funds, directors, government agencies and creditors to implement solutions which provide the best possible outcomes.

-
 Article FRS 102 Periodic Review series: Small companiesExplore key changes to small company disclosures under FRS 102 Section 1A, including UK GAAP updates on leases, tax, going concern and related parties.
Article FRS 102 Periodic Review series: Small companiesExplore key changes to small company disclosures under FRS 102 Section 1A, including UK GAAP updates on leases, tax, going concern and related parties. -
 Audit and Assurance FRS 102 Periodic Review series: Other changesOn 27 March 2024, the Financial Reporting Council issued amendments to FRS 100 – 105 (known as GAAP, or Generally Accepted Accounting Practice), a suite of accounting standards applicable in the UK and Ireland. These are used by an estimated 3.4 million businesses in preparing their financial statements.
Audit and Assurance FRS 102 Periodic Review series: Other changesOn 27 March 2024, the Financial Reporting Council issued amendments to FRS 100 – 105 (known as GAAP, or Generally Accepted Accounting Practice), a suite of accounting standards applicable in the UK and Ireland. These are used by an estimated 3.4 million businesses in preparing their financial statements. -
 Audit and Assurance ID Verification: Economic Crime & Corporate Transparency Act 2023Companies House is introducing mandatory identity verification requirements for Directors and People with Significant Control (PSCs), as the next step towards full implementation of the Economic Crime and Corporate Transparency Act 2023.
Audit and Assurance ID Verification: Economic Crime & Corporate Transparency Act 2023Companies House is introducing mandatory identity verification requirements for Directors and People with Significant Control (PSCs), as the next step towards full implementation of the Economic Crime and Corporate Transparency Act 2023. -
 Audit and Assurance FRS 102 Periodic Review series: Accounting for leasesOn 27 March 2024, the Financial Reporting Council issued amendments to FRS 100 – 105 (known as GAAP, or Generally Accepted Accounting Practice), a suite of accounting standards applicable in the UK and Ireland. These are used by an estimated 3.4 million businesses in preparing their financial statements.
Audit and Assurance FRS 102 Periodic Review series: Accounting for leasesOn 27 March 2024, the Financial Reporting Council issued amendments to FRS 100 – 105 (known as GAAP, or Generally Accepted Accounting Practice), a suite of accounting standards applicable in the UK and Ireland. These are used by an estimated 3.4 million businesses in preparing their financial statements.
-
Corporate and International Tax
Northern Ireland businesses face further challenges as they operate in the only part of the UK that has a land border with a country offering a lower tax rate.
-
Employer Solutions
Our team specialises in remuneration and incentive planning and works closely with employers, shareholders and employees to ensure that business strategies are aligned and goals achieved in the most tax efficient, cost-effective manner.
-
Entrepreneur and Private Client Taxes
Our team of experienced advisors are on hand to guide you through any decision or transaction ranging from the establishment of new business ventures, to realising value on exit, to succession planning and providing for loved ones.
-
Global Mobility Services
Grant Thornton Ireland offer a different approach to managing global mobility. We have brought together specialists from our tax, global payroll, people and change and financial accounting teams across Ireland and Northern Ireland, while drawing on the knowledge and insights of our global network of over 143 offices of mobility professionals to provide you with a holistic approach to managing global mobility.
-
Outsourced Payroll
Our outsourced service provides valued service to over 150 separate PAYE schemes. These ranging from 1 to 1000 employees, working for micro, SME and global employers. The service is supported by the integrated network of tax and global mobility teams and the wider Grant Thornton network delivering a seamless service. Experienced staff deliver a personal service built around your business needs.
-
Tax Disputes and Investigations
Our Tax Disputes and Investigation team is made up of tax experts and former HMRC investigators who have years of experience in dealing with a variety of tax investigations. Our expertise and insight can guide you through all interactions, keeping your cost at a minimum while allowing you to continue with the day to day running of your business.
-
VAT and Indirect Taxes
At Grant Thornton (NI) LLP, our team helps Northern Ireland businesses manage their UK and global indirect tax risks which, as transactional taxes, can quickly become big liabilities.

The reality is that it is no longer a question of “IF”, but “WHEN” an organisation will be subject to a data or Cyber security breach.
Cyber criminals and hackers are becoming more sophisticated and even the most prepared organisations are not immune from the threat they pose. In many cases, organisations do not realise their security has been breached until long after the event has occurred.
Our Services
Our Cyber incident response service helps clients establish exactly what happened, often helping to recover stolen assets and remediate the security vulnerabilities identified during the response. We have developed bespoke tools to assist and maintain an extensive database of threats and dark web activities to keep clients informed of potential threats and how they may have been affected by them.
The incident response handling process consists of iterative processes that range from identifying the nature of incidents to implementing security measures to limit future attacks.
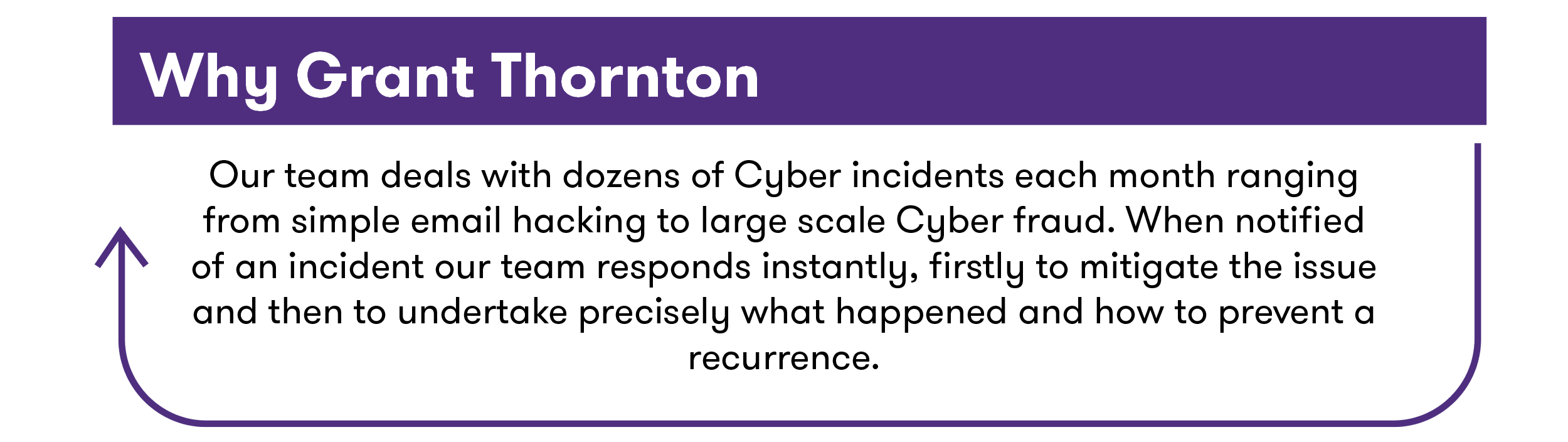
We have identified seven key steps to help you resolve any incident:
Update your subscriptions for Grant Thornton publications and events.






